jwt_hack
"/home/yossef/notes/personal/hacking/jwt_hack.md"
path: personal/hacking/jwt_hack.md
- **fileName**: jwt_hack
- **Created on**: 2025-07-21 14:18:38
in this gone talk about 10 ways to hack jwt(not hack) it's like making bug
JWTs consist of three parts:
1- Header: contains information about the type of token and the
algorithm used to sign it.
2- Payload: contains the actual claims being made, such as the user’s
identity, roles, and permissions.
3- Signature: is used to verify the authenticity of the token and ensure
that it has not been tampered with.
for more info about the token check on
jwt.ioand passing the token for
and understand how it's works by analysis what happened
if not want to use a website gone use this tools in this note
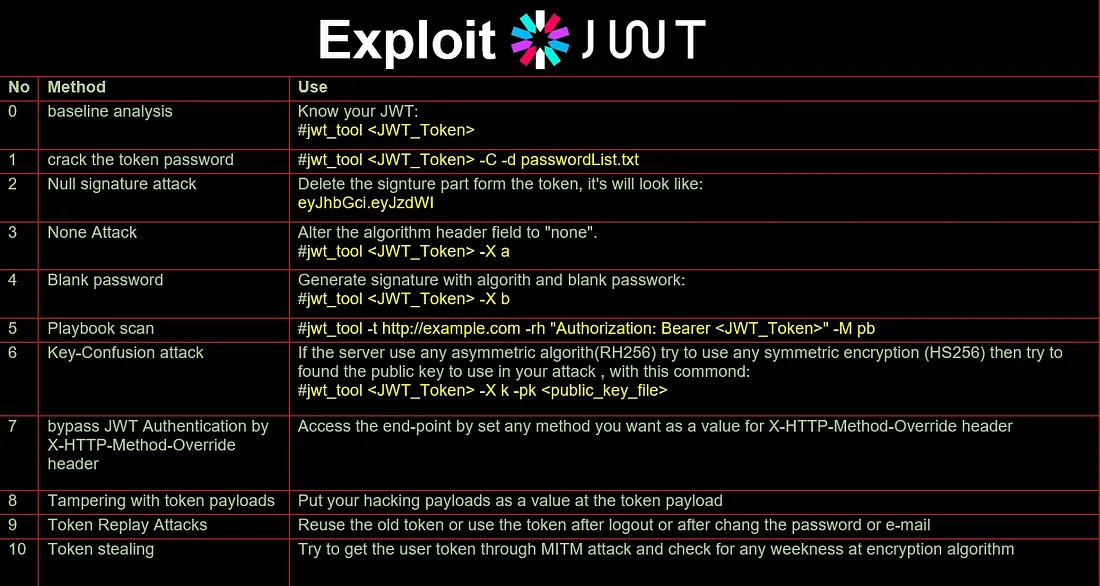
jwt_tool
- crack the token password:
./jwt_tool.py eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIi\
wibmFtZSI6Ik11c2FiIEFsaGFyYW55Iiwicm9sZSI6InVzZXIiLCJpYXQiOjE2ODc3MjI4NDl9.X3\
tG7w5QvFJ5eIetPnG8ECyM4l2E7pBcC_j9iZWY7Qg -C -d ~/hacking/password_list/\
rockyou.txt
-C, — crack crack key for an HMAC-SHA token
-d DICT, — dict DICT dictionary file for cracking
- Null signature attack:
delete the signature part, and your token will look like
./jwt_tool.py <JWT_Token> -X n
- None Attack:
try to set the algorithm header field to “none”, then encode the header
using base64-encoding, and delete the signature part then send it to the server.
If you lucky this will lead to bypassing the signature check, so you didn’t
need to crack the password.
./jwt_tool.py <JWT_Token> -X a
- Blank password: generate signature with algorithm and blank password:
Some developers misconfigure their applications and leave the JWT secret empty
(""). If that's the case, anyone can forge tokens
./jwt_tool.py <JWT_Token> -X b
- Playbook Scan: Try to manipulate all the contents of the token to scan
for common JWT vulnerabilities.
you can automate your test by this command:
./jwt_tool.py -t http://example.com -rh “Authorization: Bearer <JWT_Token>” -M pb
Test Type Description
- Weak secrets Checks if JWT is signed with weak or blank secrets.
- alg switching Tries to change the algorithm (e.g., HS256 →
none, RS256 → HS256) to bypass verification. - Payload tampering Modifies roles and values (e.g., role: user → admin)
to check if they’re enforced server-side. - Expiration bypass Tries expired tokens to test if expiry is being enforced.
- none algorithm attack Removes the signature if the server accepts
tokens with alg: none. - Replay attack test Tests token reuse behavior.
- Error-based detection Sends bad tokens to provoke errors and
learn server behavior.
- Key-Confusion attack:
If the server uses any asymmetric algorithm like RS256, this
means you need both the server’s private key and a public key
in order to accurately hash the JWT signature.
Meanwhile, HS256 is symmetric encryption, so only one key is
used for both the signature and verification of the token.
If you can discover and obtain the server’s RS256 public key,
then switch the algorithm from RS256 to HS256, there is a
chance you may be able to leverage the RS256 public key as the
HS256 key.
You will need to save the captured public key as a file on your
attacking machine. (You can simulate this attack by taking any
public key and saving it as public-key.pem.)
./jwt_tool.py <JWT_Token> -X k -pk public-key.pem
This command attempts a key confusion attack where: The original token was signed with RS256 (asymmetric). You try to trick the server by switching it to HS256 (symmetric) and using the public key as the new HMAC secret.
7 - Bypass JWT Authentication by X-HTTP-Method-Override header:
The X-HTTP-Method-Override header is used to enable HTTP methods
(verbs) in older web browsers that only support GET and POST
methods. It is also used to pass other HTTP methods to a server
that is behind aggressive firewalls which block non-GET or
non-POST requests.
You can add this header with a value of any HTTP method (e.g.,
POST, PUT, PATCH, DELETE, UPDATE, GET) while making an HTTP POST
call. A delegating handler can then intercept the method override
and take appropriate action.
This trick works in many API penetration tests and has been used
to bypass JWT authentication — including in the ESPv2 component
(CVE-2023-30845).
8 - Tampering with token payloads:
In the token payload, you can replace normal values with crafted
data containing injection payloads. These can include SQL
Injection, Cross-Site Scripting (XSS), Server-Side Template
Injection (SSTI), and more.
This technique is used to test if the server uses payload values
in insecure ways without proper validation or sanitization.
stillllllllllllllllllllllllll work here(soooooooooooon)
9 - Token Replay Attacks:
This involves reusing an old token — for example, after the user
logs out or changes their password or email. If the JWT token is
not properly invalidated or refreshed, the attacker may continue
to access the system using the same token as if they are still
logged in.
10 - Token Stealing:
If an attacker gains access to a user's JWT token, they can use
it to impersonate the user and access protected resources. This
can occur if the token is transmitted over an insecure channel
(e.g., plain HTTP) or stored insecurely on the client side (e.g.,
in localStorage or exposed in JavaScript).
How to Secure JWT:
-
Use an encrypted channel (HTTPS):
JWTs are transmitted as HTTP headers or in the request body,
so transmitting them over HTTPS ensures that the tokens are
encrypted in transit. -
Use strong keys:
JWTs are signed using a secret key, so it’s important to use a
strong key that is kept secret and not easily guessable.
Consider using a key length of at least 256 bits. -
Use an asymmetric algorithm and enforce it:
To prevent Key Confusion attacks, use asymmetric algorithms
(e.g., RS256) instead of symmetric ones like HS256. Always
verify the algorithm type on the server side. -
Implement proper token expiration:
JWTs should have a limited lifespan to prevent them from being
used indefinitely. Set a short expiration time and implement a
secure token refresh mechanism. -
Implement proper token revocation:
If a JWT is compromised or stolen, there must be a mechanism to
revoke the token and block its future use. -
Implement proper token validation:
Always validate JWTs on the server side. This includes checking
the signature, issuer (iss), audience (aud), expiration
time (exp), and algorithm (alg). -
Validate token payload data:
To prevent tampering with token payloads, ensure that payload
values are validated and not trusted blindly. Watch for
injection attacks like SQLi, XSS, or SSTI. -
Do not include sensitive data in the token:
Avoid putting sensitive or personally identifiable information
(PII) directly in the JWT payload. Use encrypted storage or
secure transport for such data instead. -
Perform regular security audits and testing:
Continuously test your authentication system to detect
vulnerabilities early. Conduct code reviews, penetration
testing, and monitor logs for abnormal JWT usage.
JWT Tools:
-
jwt_tool
https://github.com/ticarpi/jwt_tool -
jwtXploiter
https://github.com/DontPanicO/jwtXploitercontinue:./hc22000_content.md
before:./hacking_wifi_aircrack.md